How to configure a WireGuard Windows 10 VPN client
Jay Rogers
May 23rd, 2020

This post belongs to my "mini-course" on Gain flexibility & increase privacy with WireGuard VPN. I'll only be walking through how to set up a client for WireGuard on Windows 10.
If you don't have a server (or even if you already have one), definitely start from the top. I make a few assumptions and I broke things into separate posts because I try to get as detailed as possible.
If you are just here for the client configuration, keep reading!
What you'll achieve
- We will be using the official client from WireGuard on Windows 10 to connect to our WireGuard VPN server
- All Internet traffic on the Windows 10 Client will pass through our WireGuard VPN first, then access the Internet
Here is what this looks like:
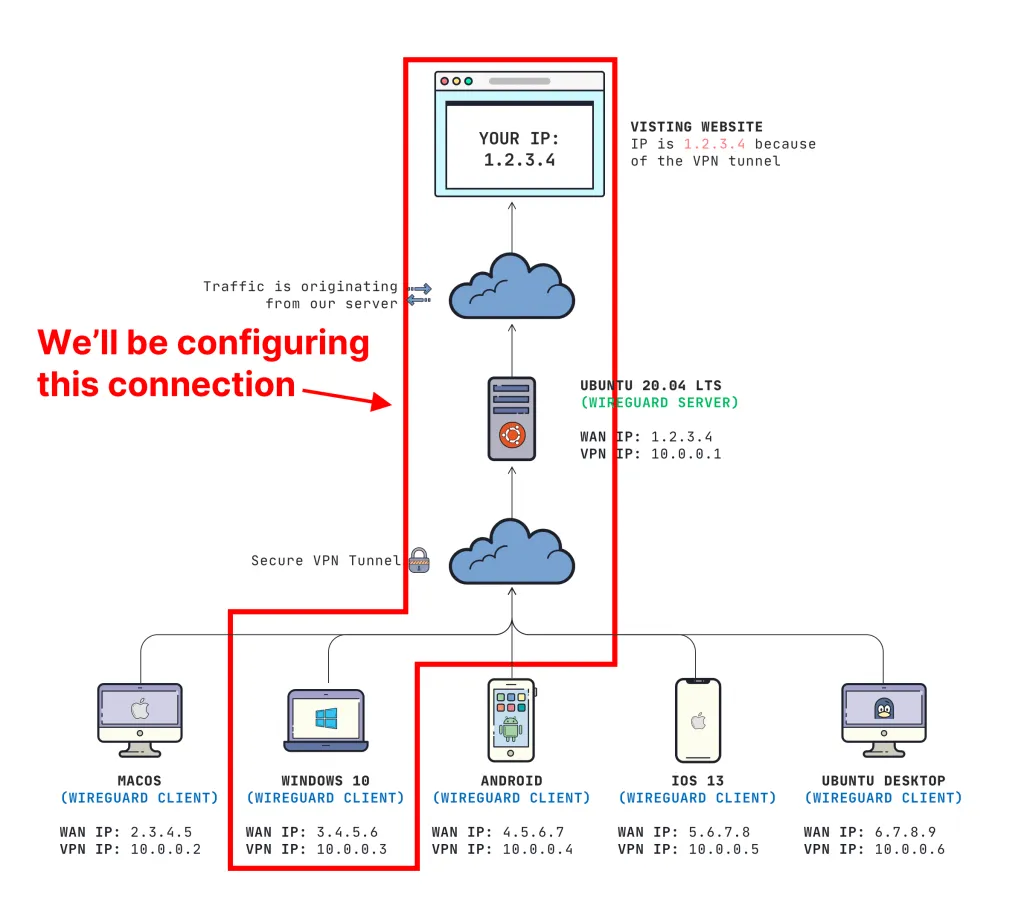
Prerequisites
- You need a working WireGuard Server (learn how to set that up here)
- You need a Windows 10 computer with admin privileges for install
- The user must also be apart of the local admins group to run the VPN connection (thanks to /u/dubtea on Reddit)
- Admin privileges are no longer required on version 0.3.1 or higher
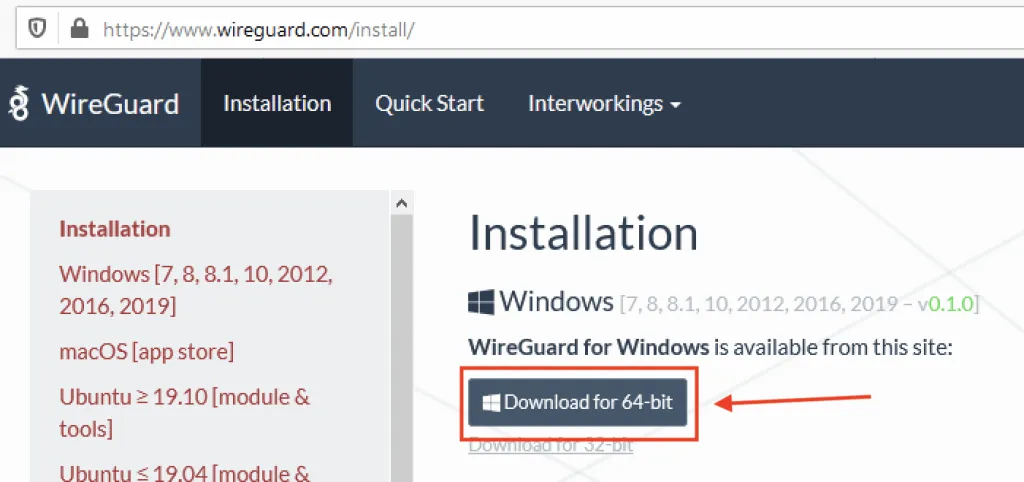
Download the WireGuard Client
Always download clients from official sources. You can find that here: https://www.wireguard.com/install/
Install & Configure
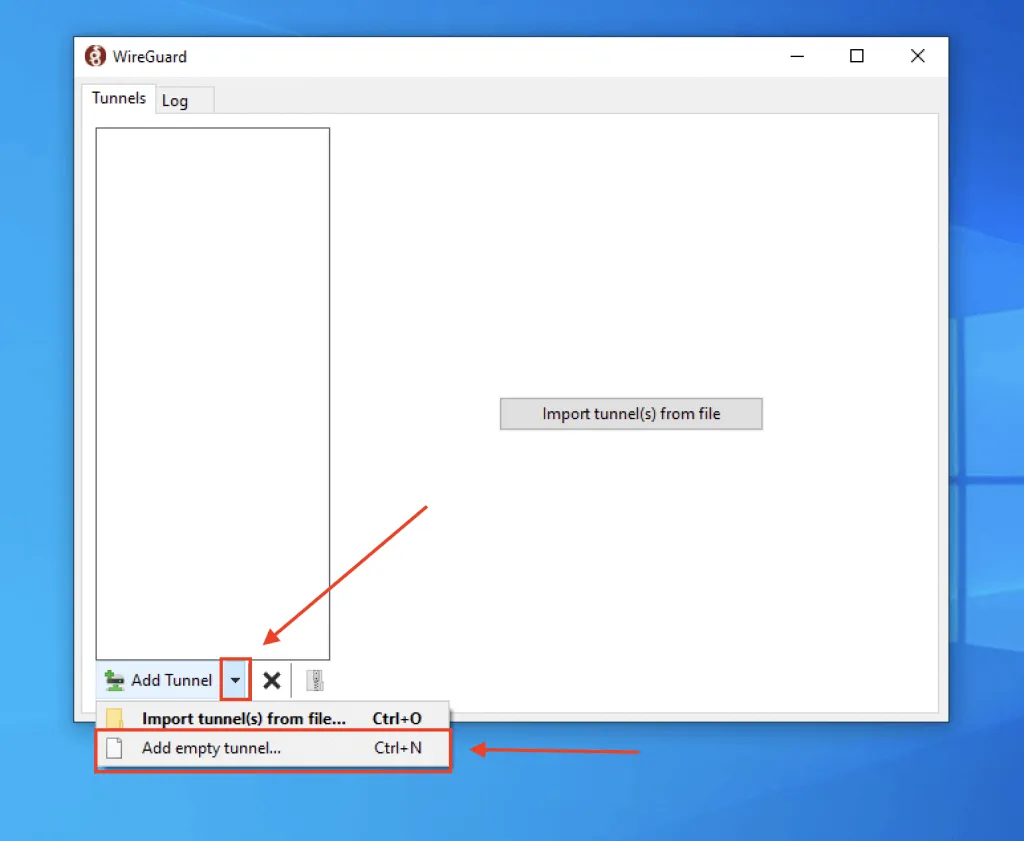
Once you install the client, you will want to click the arrow next to "Add Tunnel", then click Add empty tunnnel....
What's nice about this is the GUI creates a public and private key for us automatically.
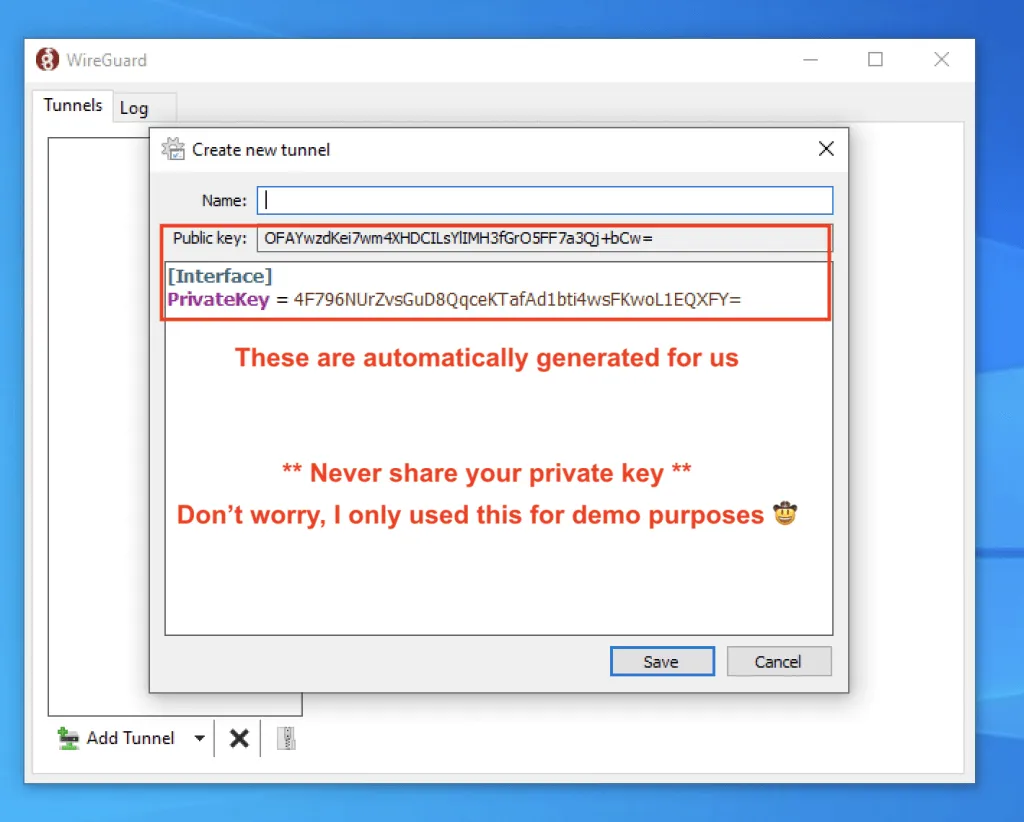
We're far from done, so let's get it to connect to our server.
Expanding the configuration
We need to update the configuration file to look like this:
wg0.conf
[Interface]
PrivateKey = abcdefghijklmnopqrstuvwxyz1234567890=+
Address = 10.0.0.3/24
DNS = 1.1.1.1, 1.0.0.1
[Peer]
PublicKey = YOUR_SERVER_PUBLIC_KEY
AllowedIPs = 0.0.0.0/0
Endpoint = YOUR_SERVER_WAN_IP:51820
IMPORTANT: You need to replace YOUR_SERVER_PUBLIC_KEY and YOUR_SERVER_WAN_IP
I dive into detail what this all means in another post, but make sure you are also setting your Address to a unique IP address on your virtual private network.
This is what mine looks like (again, never share your private key. This is just a demo):
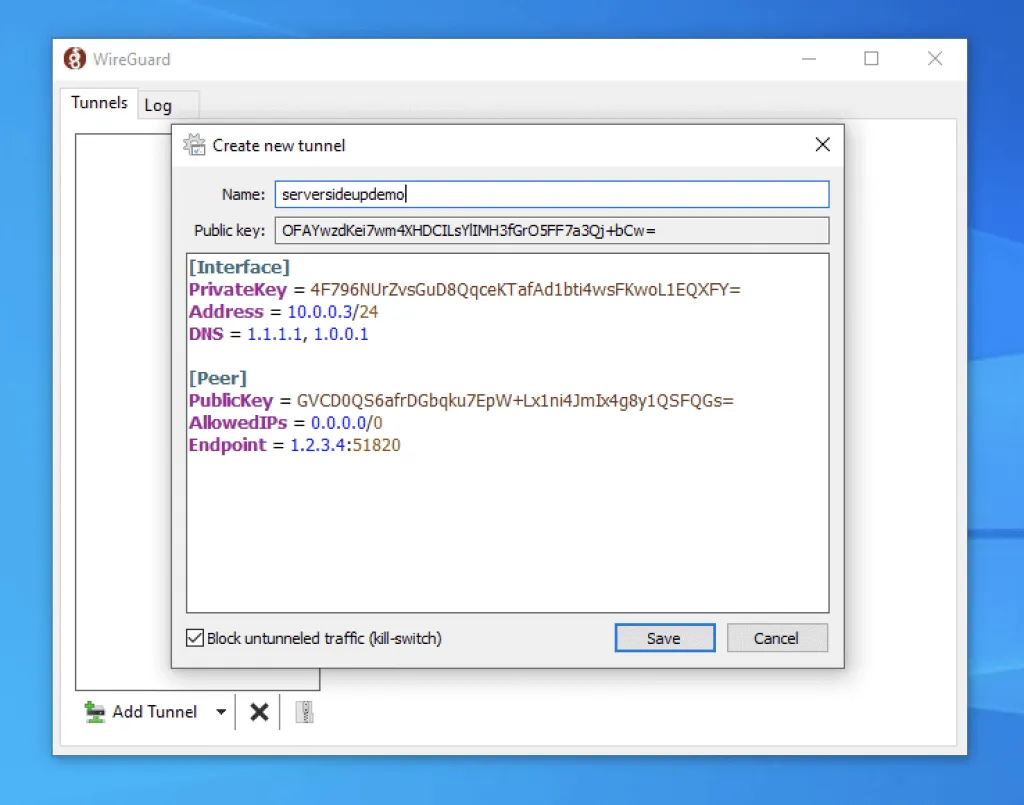
Checking Block untunneled traffic will make sure that all of our traffic is being routed through our VPN.
Add your client key to your server
If you press Activate on the next screen, it will not connect. Your server needs to know who you are.
Adding your client's public key to the server
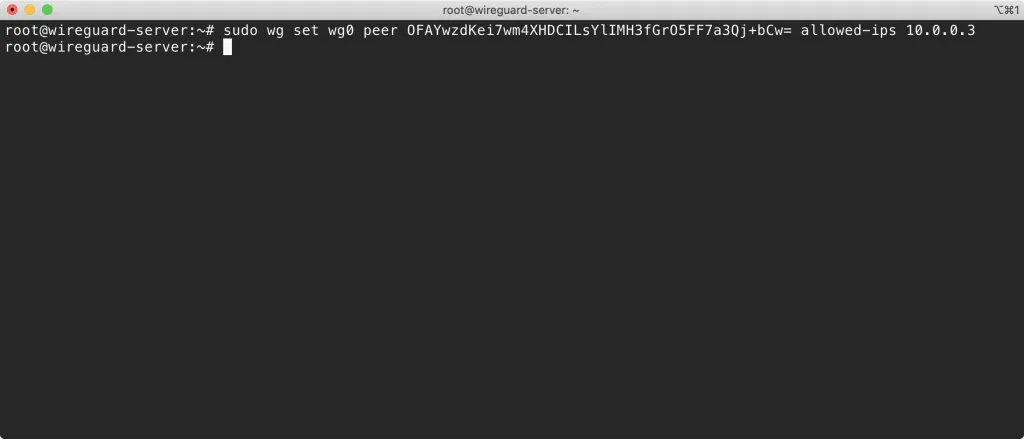
The easiest way to add your key to your server is through the wg set command.
ON YOUR SERVER run this command:
Add client to server
sudo wg set wg0 peer YOUR_CLIENT_PUBLIC_KEY allowed-ips YOUR_CLIENT_VPN_IP
IMPORTANT: You need to replace YOUR_CLIENT_PUBLIC_KEY and YOUR_CLIENT_VPN_IP
You can compare my command below to my diagram at the top of my post for exactly what I mean:
Test your connection
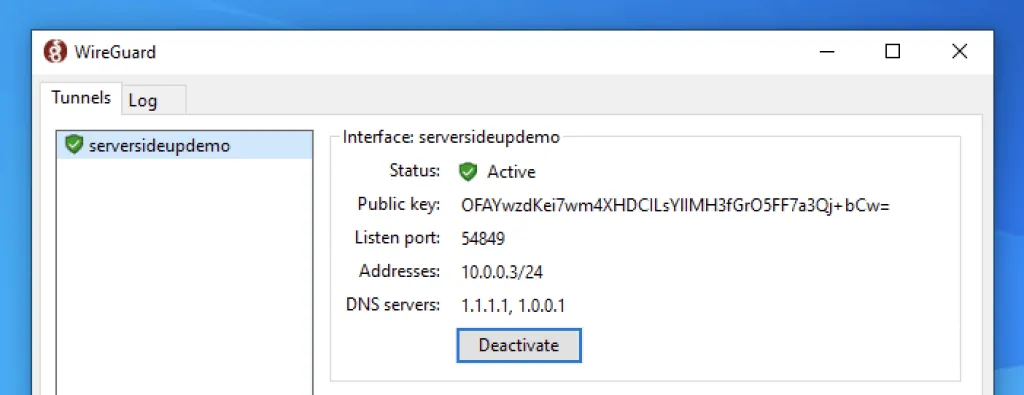
On your Windows 10 machine, press the Activate button. You should see a successful connection be made:
Once you are connected, head on over to dnsleaktest.com. This will tell you two things:
- Is your DNS "leaking" (using a different DNS provider outside of your VPN)?
- Is your IP Address different?
If you followed my configuration, all DNS tests should comeback using "CloudFlare".
Test the DNS Leak with WireGuard VPN active and inactive. Compare the results.
The last place to run a test is fast.com. This will run a speed test of your connection. If you run notice a dramatic decline in speed, try setting up a server in a region that is close to you (where you will usually be connecting from). I've always had good luck with Digital Ocean, Vultr, and Linode.
That's all!
If you have any other clients to configure, check out my "mini-course" where you can learn to configure macOS, iOS, Android and more with WireGuard VPN.
Any questions, just let me know! You can add them to the comments below or ask me on Twitter. If you like posts like this, you can get more of them if you sign up on our mailing list.
Want to work together?
Professional developers choose Server Side Up to ship quality applications without surrendering control. Explore our tools and resources or work directly with us.

Join our community
We're a community of 3,000+ members help each other level up our development skills.
Platinum Sponsors
Active Discord Members
We help each other through the challenges and share our knowledge when we learn something cool.
Stars on GitHub
Our community is active and growing.
Newsletter Subscribers
We send periodic updates what we're learning and what new tools are available. No spam. No BS.
Sign up for our newsletter
Be the first to know about our latest releases and product updates.